nft命令增加IP协议类型的表pcap-test,由于默认类型为IP,可以不指定类型,其它支持的类型有:ip6/arp/bridge/inet/netdev。之后,增加两个链localin-test和localout-test,类型为filter,挂载点分别为input和output。
# nft add table ip pcap-test # nft add chain pcap-test localin-test { type filter hook input priority 0\; } # nft add chain pcap-test localout-test { type filter hook output priority 0\; } # # # nft list tables table ip pcap-test # # nft list chains table ip pcap-test { chain localin-test { type filter hook input priority filter; policy accept; } chain localout-test { type filter hook output priority filter; policy accept; } } 在pcap-test表中增加如下规则,将端口80相关报文,记录日志,指定netlink组为30。
# nft add rule pcap-test localin-test tcp dport 80 ct mark set 1 # nft add rule pcap-test localout-test tcp sport 80 ct mark set 1 # # nft add rule pcap-test localin-test ct mark 1 log group 30 # nft add rule pcap-test localout-test ct mark 1 log group 30 # # # nft list ruleset table ip pcap-test { chain localin-test { type filter hook input priority filter; policy accept; tcp dport 80 ct mark set 0x00000001 ct mark 0x00000001 log group 30 } chain localout-test { type filter hook output priority filter; policy accept; tcp sport 80 ct mark set 0x00000001 ct mark 0x00000001 log group 30 } } 使用tcpdump抓取报文,组指定为以上的30:
# tcpdump -i nflog:30 -w nft-port80.pcap tcpdump: listening on nflog:30, link-type NFLOG (Linux netfilter log messages), capture size 262144 bytes ^C6 packets captured 6 packets received by filter 0 packets dropped by kernel 在input挂载点,抓取的报文如下,首先是netfilter的日志头部信息,包括hook点,接口索引等;最后的PAYLOAD部分包含原始的数据报文。

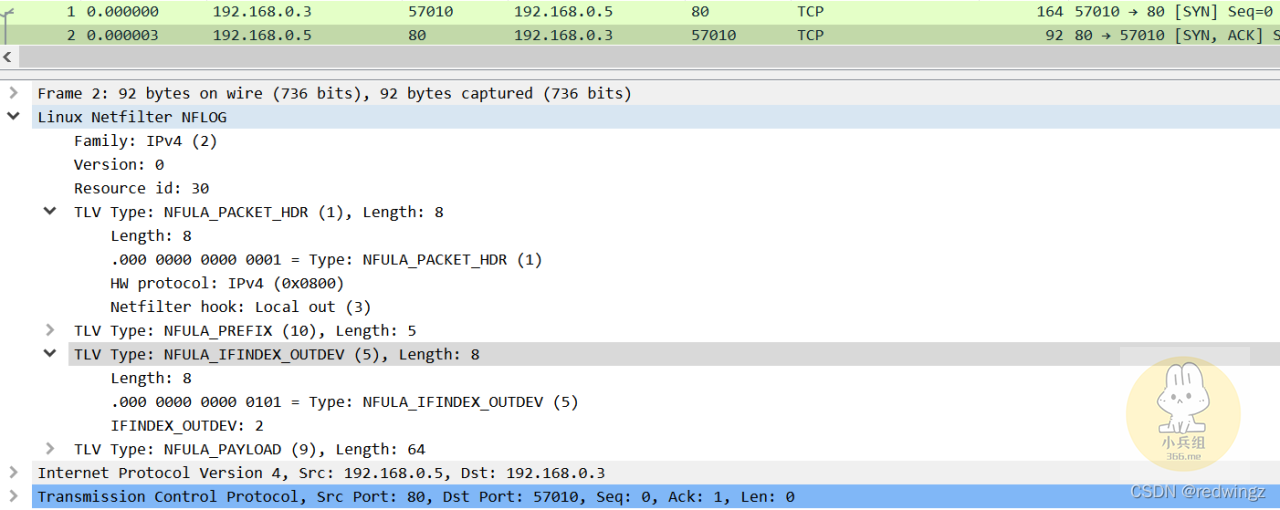
以下为output挂载点抓取的报文:
Visited 2 times, 1 visit(s) today
声明:本站所有文章,如无特殊说明或标注,均为本站原创发布。任何个人或组织,在未征得本站同意时,禁止复制、盗用、采集、发布本站内容到任何网站、书籍等各类媒体平台。如若本站内容侵犯了原著者的合法权益,可联系我们进行处理。

